Each security solution we deploy is custom tailored to meet the needs of the customer.
We implement 100% auditable access control methods incorporating cutting-edge biometrics & high definition IP video surveillance
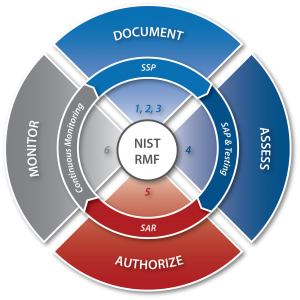
We develop in-depth security policy aimed at meeting organizational security goals & achieving compliance
We assist with DoD/ IC / Federal security requirements evaluation, solution generation, & solution implementation
We securely configure servers, IP devices, workstations, mobile phones, and Internet of Things devices
We provide automated continuous monitoring solutions which actively scan systems for vulnerabilities, & alerts to anomalies